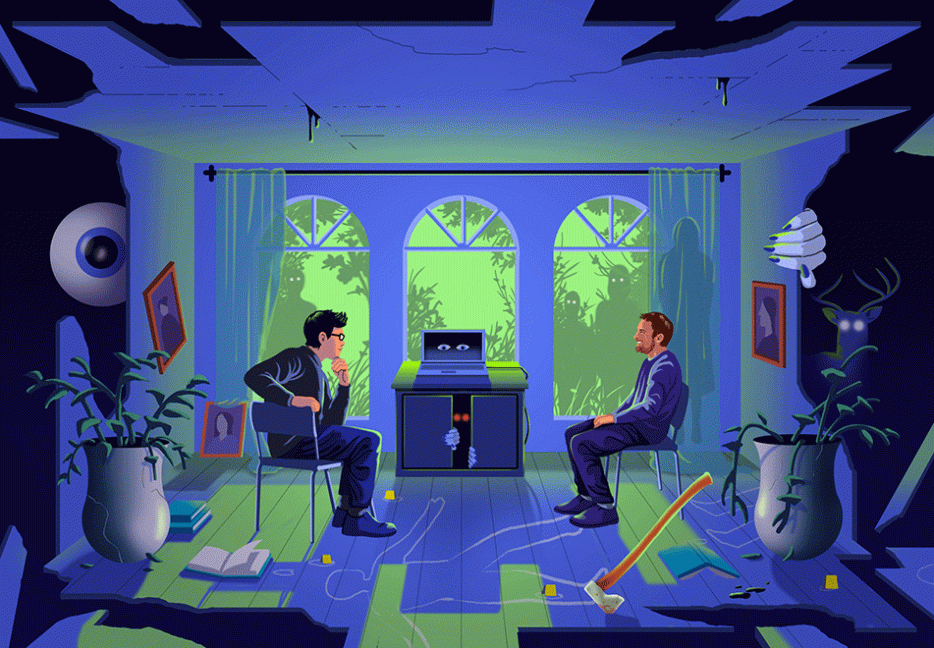
Michael Seidlinger and I met years ago, in the apocalyptic landscape of a semi-aborted writing conference, just before the COVID-19 pandemic had become official. We bumped elbows, unwitting and maskless, and joked about the barren conference centre. We were in high spirits; I had just signed my first book contract, and neither of us knew what was to come.
Two years later, we'd both released literary horror books: Seidlinger’s Anybody Home? (CLASH Books), the harrowing tale of a gang of home invaders who psychologically destroy a family from the inside out, and my own The Deer (Dalkey Archive Press) , a surrealist psychological thriller in the aftermath of a fatal car accident. A common interest in how technology is affecting our memory and sense of security brought us back together. Below, Seidlinger and I touch on everything from the inner voyeuristic desire, to computer hacking, to our changing online identities.
—Dashiel Carrera
Dashiel Carrera: Firstly, how did you become interested in home invasions?
Michael Seidlinger: Home invasions are one of the few things that still scare me. I find most horror—although it can be creepy, it can be dark, it can be outlandish, it can be a gore fest—nothing really “scares me” quite like home invasions. It’s actually something that will keep me up at night when done well. And I think it’s because it’s something that can actually happen to any one of us, even people living in an apartment. It can still happen to you. If you have a house, a home, there’s the potential for someone to invade it. And like a serial killer, invasions displace that power and control over a space that should be yours, a space that should be like a second skin, you know, where we can actually be comfortable. A home invader can switch it up so vastly by virtue of breaking in and being an unwanted guest.
DC: Home invasions are my greatest fear.
MS: Do you live in a house or an apartment? Just out of curiosity.
DC: I live in a split-up duplex in downtown Toronto.
MS: You’ve got a slight cushion because it’s probably less likely to happen in a duplex, but you never really know. You know, that’s the thing. That’s what’s scary about it.
DC: It seems like every manner of horror is just a Google search away these days, but I’m always secure in knowing these horrible things are happening outside my home. But if I lost my sense of safety in my home? I don’t know what I’d do.
MS: I encountered someone while on tour for the book that told me about how they experienced one. I asked them, like, are they ever able to reclaim that space as their own? Because it does create a trauma that prevents you from being comfortable in a space that was a sanctuary and is now this lingering menace. And they said, “No, not really.” I mean, they’ve got to get back to life. But from that point on, there’ll always be a little bit more tension, an underlying sort of unease, not being able to completely settle into any home. Home is never the same. They were never able to fully reclaim that calm, even when they moved to a different spot, a completely different space. There was always this underlying feeling like, “I’m never really safe.” And that’s the scary shit right there, man.
It also comes down to technology and surveillance, the latter as a sudden necessity. We use technology to create that safe space, but it’s a two-way street. It’s a Catch-22 in many ways; technology can be used against us. In fact, it probably is used against us even more than we use it to save ourselves.
DC: Absolutely. Surveillance is wielded like a weapon nowadays. When a cop is abusing their power, everyone’s first instinct is to take out their phone and start videotaping. It’s a war of information where whoever has more footage is named the victor. Peculiar, though, because we also self-document and surveil ourselves so much on social media.
MS: There’s a war of technology, and it kind of goes back to power, right? The sense of having that technology and being able to use it. It brings me back to the nature of a hacker, for instance. Half the time, a hacker is motivated because they want to be able to prove that they can do it. There’s something they can get by virtue of their ability to reverse engineer and understand whatever encryption or stuff that keeps that thing, whatever that thing may be, away from them. It’s almost like a dare or something, being able to do it, to hack into something and claim that as their own. It’s got to be a rush. I’m sure you have more concrete, recent examples of all kinds of stuff like this, but I of course go back to Anonymous [from 4chan], the online group of initially anonymous people working together to hack and cause mischief. They were successful—hacking credit card companies, websites, the PlayStation Network, seemingly just because they could. Like, that’s the definition of power over something that isn’t yours and shouldn’t be yours. Right? It’s everywhere, man. It’s everywhere. Even if it’s social media, if it’s in our homes.
DC: Sure. I was into computer hacking a bit when I was a kid, actually. I never did anything dramatic, but I used to pull pranks. Making the school computer talk to people while they were using it, things like that.
MS: Really? Are there tools that a hacker can use? I mean, I’m sure there are tools, but are there, I don’t know, engines or middleware solutions for hackers? Like some app or client that can literally be like “password destroyer.exe” and hackers use it to run scripts and break into people’s accounts with ease? I’m curious: what does a hacker use to hack?
DC: Honestly, there are more toolkits than you might imagine. I haven’t been up on this stuff in a while, but Cain and Abel used to be a big one for monitoring and sniffing out data on local networks. Basically, it would redirect data flow so anything happening on a local network would start flowing through your computer. There’s also a big cybersecurity community out there which is always looking to find software vulnerabilities, and not all of them have pure intentions. The usual breakdown is that “white hat” hackers find vulnerabilities so they can report them and get them fixed, “grey hat” hackers find vulnerabilities and don’t care what happens, and “black hat” hackers find vulnerabilities to maliciously download personal information, or pull some other scam. A lot of the exploit databases and hacking tools out there are meant for security administrators rather than hackers, but end up getting used maliciously.
MS: It’s so poetic. The security system, like any form of technology, when overused or misused…I think it’s a lesson. Too much of anything is a bad thing.
DC: Absolutely. Even more strange is that it has to be that way. Any security system needs to have some kind of backdoor, otherwise we risk locking ourselves out forever. Just like how even though cars have strong windows, they can’t be so strong that people can’t kick them out if they careen into a river and need to escape.
MS: I randomly just thought of this one episode from King of the Hill involving the character Dale Gribble, the paranoid conspiracy theorist of the group. The group goes to Tijuana because they couldn’t find their favourite Alamo beer anywhere in Texas. Turns out the beer was on recall because some soap got in the batch, but they didn’t recall it in Mexico. They end up drinking the tainted beer and rushing back home in a flurry due to, well, what happens when you get food poisoning. They’re all running into their own respective homes. Dale is running into his safe-haven basement, barely able to hold all that is trying to come out, but he has some wild five-factor security code system attached to his door. So he ends up going through all those phases just to get to a working toilet. Go too far, and the home and the technology work against you.
DC: A couple of days ago, I stayed up all night watching surveillance footage of carjackings in Toronto, which apparently are up this summer since COVID-19 restrictions were lifted. My question for you is: why did I do that? Your book seems to imply that there’s some innate lust to watch this kind of footage that might obliquely encourage these crimes.
MS: I think a lot of that comes down to our curiosity, right? It’s like what you said: there’s been a surge, you’re explaining the footage and why you’re watching it, and I immediately think, “ooh, I wonder…who is it?” Is this a trend? An onset of carjackers that would be more insidious? It’s that brand of curiosity. We naturally want to know why.
DC: Yes, curiosity and an attempt to solve some kind of puzzle. I wonder if we have some subconscious sense that we’ll be able to come up with a reason why what happened to the victims won’t happen to us.
MS: Exactly. It’s a puzzle. It’s a mystery that you want to solve.
DC: The other day, I saw someone running full speed through the streets of downtown Toronto with what looked like one of those ice scrapers used to wipe the snow from your car. About half a block behind, someone was chasing him, yelling, “Hey, man! Stop! That’s not cool!” It left me with so many questions. Why would anyone steal an ice scraper? And why would anyone chase someone to try and get their ice scraper back?
MS: Unless the guy was running away or tried to use it as a weapon—maybe he stole cash or something or had something in his pockets? There are so many questions. And that leads right back to what we were talking about with the nature of the mystery, the puzzle. We’re kind of messed up as a species; we have the ability to sit there and rubberneck, watching as someone else becomes the victim of something.
DC: Do you know what social engineering is?
MS: Hmm, I think so? But I’d love to hear more.
DC: It’s a form of hacking that doesn’t involve any technological know-how. You collect information about the inner workings of an organization and use that information to pressure or infiltrate the organization. There was a string of celebrity Twitter account hacks last year—Elon Musk, Kim Kardashian, Kanye—that used that method. A seventeen-year-old in Florida infiltrated the Twitter group chat and learned just enough to impersonate one of their employees. An acute understanding of human nature can be used to dismantle a social system.
MS: So, there are two types of home invasions. There’s the one that would be called “breaking and entering”: The invaders are trying to steal shit. It’s an act of desperation. And then there’s the one that we’ve been talking about—invaders seeking a power dynamic. It’s about wanting to get in and inhabit the space. The first half of my book is all about social engineering; the invaders use all channels they’ve got, including social media, to get to know the father, the mother, the son. That’s as important as pulling off the actual invasion, because what’s the point in just invading some stranger? Like, you want to know what you’re taking. That’s power with a capital P. And it’s totally social engineering.
DC: There’s also a bit in your book about how social media can be used for social engineering. Can you talk a bit more about that?
MS: Yeah, absolutely. I feel like social media is a primary tool for social engineering. I mean, what is a person actively building a “brand” on Twitter or Instagram doing? They’re taking part in the act of being formed and “engineered” into someone that can be easily seen online and made into a commodity. Most people that use social media don’t even realize they are seeking validation. They’ve fallen into a feedback loop that inherently makes them think, “This is what I am supposed to do, right? This is how I become a person. This is how I become an important person. This is how I live a life.” You can’t just go to an event like a party or watch a movie without tweeting your opinions about that movie, or taking a selfie in front of the theatrical poster. Or doing a TikTok about it afterwards, being like, “Oh, it was so amazing. Best thing ever,” or “This movie sucks.” To be someone and do something, you have to document it. And all those tweets and posts end up being a paper trail.
DC: Yeah, and it freaks me out that we’ve come to associate any paper trail we can find on the internet or Google search results as a true representation of who a person is, when so many of those results are shaped by algorithmic sorting methods or unverified postings. Actually, here’s an example—on the same road trip that sparked the idea for The Deer, I got caught speeding in North Carolina. I was going something like sixty-two in a 45 zone, which ended up being just enough for a misdemeanour speeding charge down there. They dropped the charge because I was young and had only recently learned to drive, but a few weeks later, I noticed some criminal records website had posted a page about me saying I had been charged with a misdemeanour in North Carolina without mentioning what the charge was for. Took me forever to track them down and get them to remove it.
MS: It is very interesting, thinking about paper trails. I feel like naturally, the human mind might go towards forgetting the whole analogy of glass-half-empty, glass-half-full. We as a species tend to lean a bit more towards the negative. Even with the paper trail, be it Google or something else, it’s awesome to type in your name and see all these reviews of your books and all the cool things you’ve done, right? But at the same rate, how often are we thinking about that versus, you know, typing your name in and then some embarrassing [thing pops up] like, “Oh, here’s my high school term paper.” It’s wild to me.
I’m very curious about your thoughts on memory in terms of human recollection in our modern day—you know, content, heavy content, everything’s content, everything’s being documented, and we’re really connected. But we’re also surveilled through our various social media channels, through email, through everything. We don’t have to remember anything, right? I’m curious about your thoughts on that—like, in terms of our memory becoming less like a hard drive and more like RAM. It’s more temporary, and then it gets documented online, and then we keep moving on. I’m curious about your thoughts on our current, and maybe continuous, moment in time with regards to memory and technology.
DC: Yeah, absolutely. My spelling has gone downhill as a result of spellcheckers. And I absolutely tend not try to remember anything because I assume I can always just Google it again later. But I often worry I’m missing out in some way. There’s a good amount of research that suggests that when you have to memorize something, you end up “chunking” it, and that this process of forcing yourself to break it down shapes your thinking. I wonder if the fact that we have less of an impulse to remember nowadays means we have less of an impulse to listen, as well. Because there’s no urgency to really absorb other information, we end up sifting through it impressionistically, never having to seriously confront any information that contradicts our belief systems.
It reminds me of an old project I did after that Slate article came out, “You Won’t Finish This Article.” The article argues that most people online never read past the first sentence, so I tried to imagine what it might be like for someone in the digital age to develop an impression on a topic. I ran a Google News search for the words “terror” and “terrorism,” took the first sentence from each article and rearranged it into a collage style non-fiction piece to create an impression of how someone might develop an [understanding] of terrorism in a single week. While information we consume comes from the internet, I think we rely on ourselves, more than ever, to be the ones that carve out the narrative from the sea of information. That’s why I think fiction is important now more than ever: it forces us to reconsider how we create these narratives, and push to find new ways of thinking beyond what’s immediately presented to us by new digital platforms.